Theory and ModelingDefinitions of Traffic Management Mechanisms The goal of Deliverable D2.2 "Report on Definitions of Traffic Management Mechanisms and Initial Evaluation Results" is to propose and
justify traffic management solutions and to provide models for the
evaluation of the proposed mechanisms for subsequent performance
evaluation. To cover a wide set of mechanisms w.r.t. the scope of the
project, each partner was asked to propose traffic management solutions.
Since partners have either academic or corporate background, a wide set
of solutions was received. The solutions have been compared and mapped to the
scenarios considered in the SmartenIT project as they have been identified in WP1. Moreover synergies between
the solutions have been investigated in order to discover potential overlaps or complements. The subsequent performance evaluation of the solutions
can then be performed for a set of solutions that share a common use
case. Furthermore the identified synergies will support the development of a
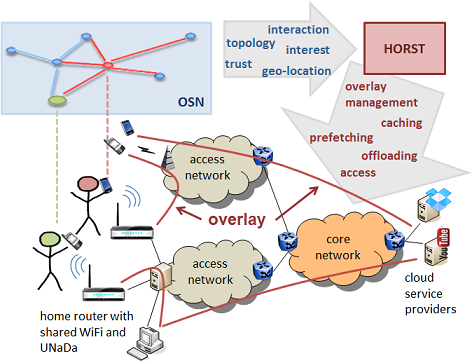
SmartenIT solution which will be composed by a set of the proposed mechanisms. Example Traffic Management Approach: Home Router Sharing based on Trust (HORST) Home router sharing based on trust (HORST) [1] is such a mechanism which addresses three use cases: data offloading, content caching/prefetching, and content delivery. The HORST mechanism eases data offloading to WiFi by sharing WiFi networks among trusted friends. Moreover, it places the content near to the end user such that users can access it with less delay and higher speed, which generally results in a higher Quality-of-Experience. The SmartenIT solution consists of a firmware for a home router, an OSN application, and a mobile device app. The HORST firmware establishes a private and a shared WiFi network (with different SSIDs) and manages the local storage of the home router as a cache. In order to participate, a user needs a flat rate Internet access at home, he has to install the HORST firmware to his home router, and he needs to install an application to his mobile device. The owner of the home router uploads the WiFi access information of the shared WiFi to the OSN application. Each user can share his WiFi information to other trusted users via the app and request access to other shared WiFis. As the application knows the position of the users, it can recommend WiFis near to the users, or automatically request access and connect the users for data offloading. Social cascades will be used to predict which content will be requested by which user. As the application also knows about the current and future users of each WiFi, the UNaDa on the home router can be used to cache or prefetch delay-tolerant content which will be delivered when the user is connected to the WiFi. The application on the mobile device of users sends social information (location, activity patterns, and interest) to the HORST system on its own router. Thus, private data of the user stays on its own devices. Additionally, the HORST router has a social monitor component to collect social information from an online social network about the router’s owner and his trusted friends. If a user approaches the home router of a trusted friend, he is provided with access data via the mobile application to connect to the shared WiFi. After the user has connected, the friend’s home router sends a notification to the users own router. Every HORST system predicts the content consumption (i.e., when and where will which content be requested) of his owner based on location, activity patterns, interests, and information from the online social network such as content popularity and spreading. If a predicted content is not yet available in the local cache, it will be prefetched. If the user is connected to a friend’s home router, a prefetch command is sent to the HORST system on the friend’s router. For prefetching as well as for actual requests which cannot be served locally, HORST chooses the best source (either another HORST home router or a cloud source) based on overlay information and traffic measurements, and fetches the desired content. In regular intervals, HORST checks if the content in his own local cache is still relevant (either for local consumption or as a source for content delivery) and decides whether to keep or replace it. Finally, HORST federates all UNaDas to form an overlay content delivery network (CDN), which allows for efficient content placement and traffic management. Thereby, ISP costs can be included in the local decisions at a UNaDa, e.g., by taking into account the location of contents in terms of Autonomous Systems (AS). A similar approach is adopted by the Socially-aware Efficient Content Delivery (SECD) mechanism [4], also developed within SmartenIT. In particular, SECD employs both social information, i.e. relationships in the social graph and users’ interests, and AS information to construct overlays, within which content items (i.e. videos) are being disseminated. To this end, information (such as home router location, cache content, prefetch commands) is stored in the overlay and HORST conducts (active or passive) traffic measurements between the end-points. For the communication between the uNaDas and the distributed storage of meta-information, the RB-Tracker [3] is used due to its efficiency. Thus, RB-Tracker builds the basis of HORST and hides the complexity of the overlay management. HORST’s system architecture requires the contribution of resources of end users, which needs an appropriate incentive. From the stakeholders, end users sticks out, as they are consumers of the services provided by the business-driven stakeholders such as ISPs. Therefore, besides monetary incentives, raising QoE of the end users and thus the perceived quality of the service works as an incentive for this group of stakeholders. HORST ensures resource contribution by incorporating an incentive mechanism coupling different resource contributions of end users to the system, namely the provisioning of storage capacity and offloading capacity, to the receivable QoE, based on the vINCENT incentive mechanism presented in [2]. In order to enhance the overall system performance, the incentive includes social networking data as a base of trust, thus increasing market liquidity.
In particular, D2.3 provides an outline of the SmartenIT ecosystem, the stakeholders, and their roles and it describes the two scenarios, EFS and OFS, addressed in WP1. Moreover, D2.3 provides a description of the use cases identified to highlight the relevance of the proposed SmartenIT traffic management mechanisms with respect to the aforementioned scenarios. The description is based on a template, which allows for an efficient description of single a use case and a coherent comparison among different use cases. A description of each use case provides information about the use case goals, the stakeholders and their interests and incentives, and the associated traffic management mechanisms. Among the proposed use cases, an initial set of use cases is selected to prioritize further work on mechanisms specification and implementation in WP3. Then, a methodology is proposed to describe the parameters and metrics to assess the performance of the use cases. An initial set of parameters and metrics associated to each selected use case is provided. Deliverable D2.3 addresses several SMART objectives, as described in SmartenIT Description of Work, by documenting the work performed in Task 2.2. The work presented in Deliverable D2.3 will be further evolved in the next phases of the project, and it will be finalized and concluded in Deliverable D2.5 “Report on Definition of Use-cases and Parameters (Final Version)”, which will be delivered at Month 30 (April 2015) of the project. Definitions of Traffic Management Mechanisms (Final version)The goals of Deliverable D2.4 "Final Specifications of Traffic Management Mechanisms and Evaluation Results" are as follows:
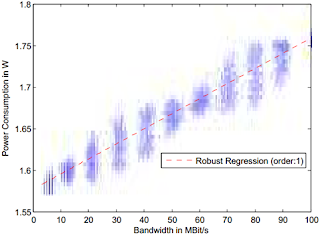
In particular, by means of the development and study of new mathematical models, we investigate a multitude of technical issues such as the effectiveness of caching in the case of distributed cloud-based content delivery systems, content demand in online social networks and its topological characteristics, power consumption of either specific equipment (such as the Raspberry Pi) or activity (such a mobile data transmissions), effectiveness and impact of VM migration and cloud federation. For instance, the figure on the left depicts the power consumption of the Raspberry Pi (device used as uNaDa) w.r.t. CPU utilization as obtained by means of the theoretical model developed in the context of Task 2.4. Moreover, these models will facilitate the evaluation of (certain aspects of) the traffic management mechanisms. Additionally, investigation of incentives for cloud federation and resource sharing, either in datacenters, or in network-edge nodes, is performed. Especially, concerning the cloud federation, new economic models including pricing schemes and tariffs are under development. Furthermore, based on the consideration of economic and business dependencies, which was initiated in D1.1, and continued in D2.2, we investigate appropriate business models involving Cloud Service Providers, Data Center Operators and Network Operators (or ISPs).
In D2.4, we follow and preserve the mapping of the traffic manangement mechanisms introduced in D2.2. In particular, we present and study the traffic management mechanisms and their potential synergies, namely combinations of mechanism that allow a broader coverage of the SmartenIT playfield, per scenario. For each mechanism or synergetic solution, the intelligence including major entities is described. Additionally, detailed specification including sequence diagrams and algorithms in pseudo-code is given in an appendix. Moreover, the associated parameters and metrics, and the evaluation framework for each mechanism or synergetic solution are defined, and the evaluation results obtained by means of theoretical evaluations, and simulations are presented. Finally, we discuss the coverage of the SmartenIT playfield by the developed traffic management mechanisms and the potential integration of multiple mechanisms in a cross-scenario approach. References:
|
Overview >